Over 13 billion malicious and suspicious emails were blocked in 2019, Microsoft said in a new report, adding that the volume of successful cyberattacks in countries experiencing COVID-19 outbreaks is on the rise.
"Threat actors have rapidly increased in sophistication over the past year, using techniques that make them harder to spot, threatening even the savviest targets," the tech giant wrote in its annual Digital Defense Report published in late September.
According to Microsoft, more than 1 billion of the blocked malicious and suspicious emails were URLs set up for the explicit purpose of launching a phishing credential attack.
"In past years, cybercriminals focused on malware attacks. More recently, they have shifted their focus to phishing attacks (~70%) as a more direct means to achieve their goal of harvesting people’s credentials."
Read more: Cybersecurity Effects of Coronavirus in ASEAN and the Path Ahead
The data were gathered from over 1.2 billion PCs, servers, and IoT devices that accessed Microsoft services, as well as 630 billion authentication events, 470 billion emails analyzed for threats, and more than 18 million URLs scanned.
The report identified ransomware as the most common reason behind incident response engagements from October 2019 through July 2020.
Also, it found that reconnaissance, credential harvesting, malware, and Virtual Private Network (VPN) exploits were the most common attack techniques by nation-state actors in the past year.
Microsoft warns that IoT threats are constantly expanding and evolving, with the first half of 2020 has witnessed an approximate 35% increase in total attack volume compared to the second half of 2019.
"To trick people into giving up their credentials, attackers often send emails imitating top brands," the technology company wrote.
Based on its Office 365 telemetry, the top spoofed brands used in these attacks are Microsoft, UPS, Amazon, Apple, and Zoom.
The report adds that morphing is being increasingly used across sending domains, email addresses, content templates, and URL domains to evade detection.
COVID-19-Themed Attacks
Furthermore, Microsoft says cybercriminals have been taking advantage of global concerns over COVID-19. Such campaigns have been used for targeting both consumers and industry sectors such as healthcare.
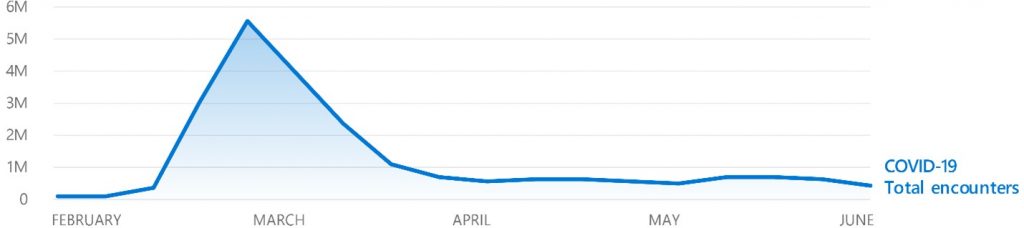
As fear and the desire for information is growing, the company is seeing an increase in the volume of successful attacks in coronavirus-affected countries.
Another finding of the report is that China, the United States, and Russia were hit the hardest but that every country in the world saw at least one COVID-19-themed attack.
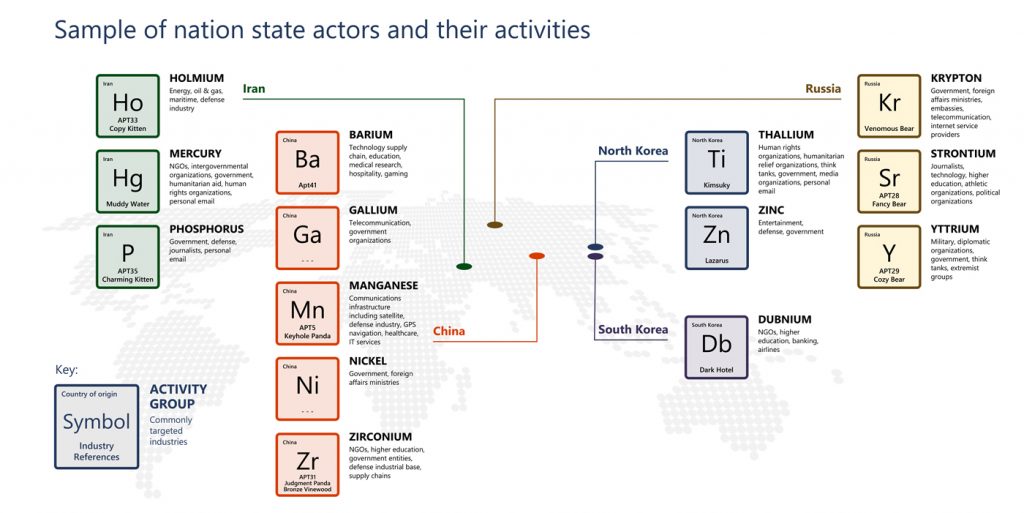
Nation-States
Nation-states have also changed targets to align with the evolving political goals in the countries where they originate, Microsoft noted.
"COVID-themed attacks targeted prominent governmental healthcare, academic, and commercial organizations to perform reconnaissance on their networks or people. In the past year, 90% of nation-state notifications have been sent to organizations that do not operate critical infrastructure─including non-governmental organizations (NGOs), advocacy groups, human rights organizations, and think tanks."
Read more: 10 Decisive Business Actions to Emerge Stronger From COVID-19
The report shows that cyber fraudsters are also targeting employees with sophisticated phishing campaigns as the work-from-home trend is accelerating and traditional security policies within an organization’s perimeter have become much more difficult to enforce.
"As organizations continue to move applications to the cloud, we’re seeing cybercriminals increase distributed denial of service (DDoS) attacks to disrupt user access and even obfuscate more malicious and harmful infiltrations of an organization’s resources."
Mary Jo Schrade, assistant general counsel at Microsoft Digital Crimes Unit in Asia, says it is fundamental to address the threats posed by the human element.
“Organizations should adopt stronger cyber hygiene practices and tools to safeguard employees and infrastructure. These include adopting multi-factor authentication, using good email hygiene (including limiting or disabling auto-forwarding of emails), timely patching and updating of apps and software, and putting in place network segmentation to keep cybercriminals from easily accessing the entire network if they do gain access," she noted.

